In this blog post, I am going to show how to deploy the application to Kubernetes from AWS ECR. There are two tasks we need to complete.
Docker Login - Create config.json file for Secret
Since we need to fetch app images from AWS ECR to Kubernetes, we need to create the secret component in Kubernetes. To do this, we need to do the following steps with the bash script.
Get the ECR password and note it.
Login to minikube with ssh
Run docker login to ECR.
aws ecr get-login-password --region us-east-1 # save it to note
minikube ssh
docker login -u AWS -p {ecr_password} 790854961075.dkr.ecr.us-east-1.amazonaws.com
cat ~/.docker/config.json
Once we log in to ECR, the file "~/.docker/config.json" is created. The login information is stored in this file. The we can create the secret component with the file.
Create Secret Component
Copy the container's ".docker/config.json" to the local and convert it to base64. Note the output.
scp -i $(minikube ssh-key) docker@$(minikube ip):.docker/config.json ./docker_config.json
cat docker_config.json | base64
Then we create the Kubernetes secret file docker-secret.yaml with the converted docker access token.
apiVersion: v1
kind: Secret
metadata:
name: my-registry-key
data:
.dockerconfigjson: {converted_password}
type: kubernetes.io/dockerconfigjson
We create the secret in Kubernetes.
kubectl apply -f docker-secret.yaml
kubectl get secret -o yaml
Besides this, there are other ways to create secrets that uses "kubectl" command.
kubectl create secret generic my-registry-key2 \
--from-file=.dockerconfigjson=docker_config.json
--type=kubernetes.io/dockerconfigjson
kubectl create secret docker-registry my-registry-key-three \
--docker-server={server address}
--docker-username={username}
--docker-password={password}
For more information, please refer here.
Configure Deployment
Finally, we can create the deployment "my-app-deployment.yaml" and deploy it.
apiVersion: apps/v1
kind: Deployment
metadata:
name: my-app
labels:
app: my-app
spec:
replicas: 1
selector:
matchLabels:
app: my-app
template:
metadata:
labels:
app: my-app
spec:
imagePullSecrets:
- name: my-registry-key
containers:
- name: my-app
image: {image_name}
imagePullPolicy: Always
ports:
- containerPort: 3000
kubectl apply -f my-app-deployment.yaml
kubectl get pod
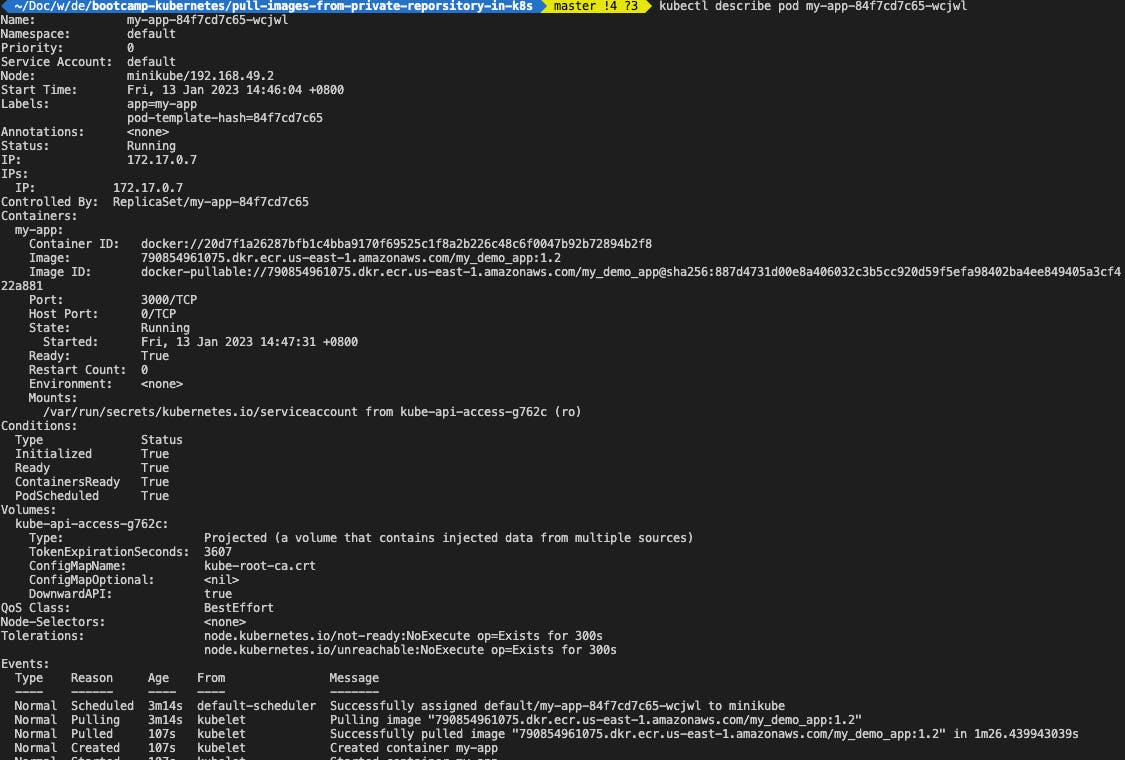
kubectl describe pod {pod_name}
Here is the log.
Summary
In this post, we demonstrated how to use deploy the application from ECR or private image registry.
Reference
Module 10 of DevOps Bootcamp
